Introducing the Ultimate Solution: Locky Ransomware Fix and Removal Guide
Understanding Locky Ransomware
Locky Ransomware is a type of ransomware that encrypts files on a user’s computer and demands a ransom for their release. It is typically spread through spam email messages containing infected attachments, such as Word documents with macros. Once the attachment is opened, Locky is able to encrypt files on the computer and change their file extension to something like “.locky” or “.zepto”.
To fix and remove Locky Ransomware, it is important to first disconnect the infected computer from any networks to prevent further spread. Then, use a reputable antivirus program to scan and remove the malware. Once the ransomware is removed, it is possible to try and recover encrypted files from backups or use a decryptor tool, although success is not guaranteed.
Remember to regularly back up important files and stay vigilant against spam emails and suspicious attachments to prevent future ransomware infections.
Steps for Locky Ransomware Removal
1. Disconnect from the internet to prevent further spread of the ransomware.
2. Identify and terminate any suspicious processes or programs related to the Locky ransomware.
3. Use a reputable antivirus or anti-malware program to scan your computer and remove any remaining traces of the ransomware.
4. Restore your files from a backup, if available. Ensure the backup was created before the infection occurred.
5. If you don’t have a backup, try using a reputable file recovery tool to retrieve encrypted files.
6. Consult online forums or security experts for specific decryption tools or instructions, as they may have developed solutions for certain versions of Locky.
7. Update your operating system and all software programs to the latest versions to patch any vulnerabilities that may have been exploited by the ransomware.
8. Enhance your security measures by installing a reliable antivirus program, regularly backing up your files, and educating yourself about safe online practices.
Remember, prevention is key. Be cautious when opening email attachments, especially from unknown senders, and keep your software up to date to minimize the risk of future ransomware infections.
Reporting Ransomware to Authorities
If you have fallen victim to a Locky ransomware attack, it is essential to report the incident to the relevant authorities. By doing so, you not only contribute to the fight against cybercrime but also increase the chances of catching and prosecuting the criminals responsible.
To report a ransomware attack, follow these steps:
1. Contact your local law enforcement agency and provide them with all relevant information, including the ransom note and any communication with the attackers.
2. Report the incident to your country’s cybercrime reporting center, such as the Internet Crime Complaint Center (IC3) in the United States.
3. Notify your antivirus software provider and provide them with any relevant details about the attack.
4. If you are part of a company or organization, inform your IT department or security team immediately.
Remember, reporting ransomware attacks is crucial in protecting others from falling victim to the same criminals. Together, we can combat ransomware and make the digital world safer for everyone.
Isolating Infected Devices
Isolating infected devices is crucial in preventing the spread of Locky ransomware and minimizing the damage caused by this encryption trojan. To isolate an infected device, follow these steps:
1. Disconnect the infected device from the network immediately to prevent further infection of other devices.
2. Disable any shared folders or network drives to prevent the ransomware from spreading to other connected devices.
3. Quarantine the infected device by disconnecting it from any external storage devices or removable media.
4. Disable macros in Word documents and exercise caution when opening any suspicious email attachments, especially those coming from unknown senders.
5. If you suspect a device is infected, scan it with reliable antivirus software to detect and remove the ransomware.
6. In the event of an infection, do not pay the ransom. Instead, seek the assistance of security experts or use reputable decryption tools provided by organizations like Bleeping Computer.
Remember, by isolating infected devices, you can contain the ransomware and protect other devices, data, and networks from being compromised.
Identifying Ransomware Infections
- Observe unusual behavior in your computer, such as:
- Files being encrypted and becoming inaccessible
- Random file extensions being added to your files
- Pop-up messages demanding ransom payment
- Sluggish performance or frequent system crashes
- Check for ransomware-related files or processes:
- Open Task Manager by pressing Ctrl+Shift+Esc
- Look for any suspicious processes with random names or high resource usage
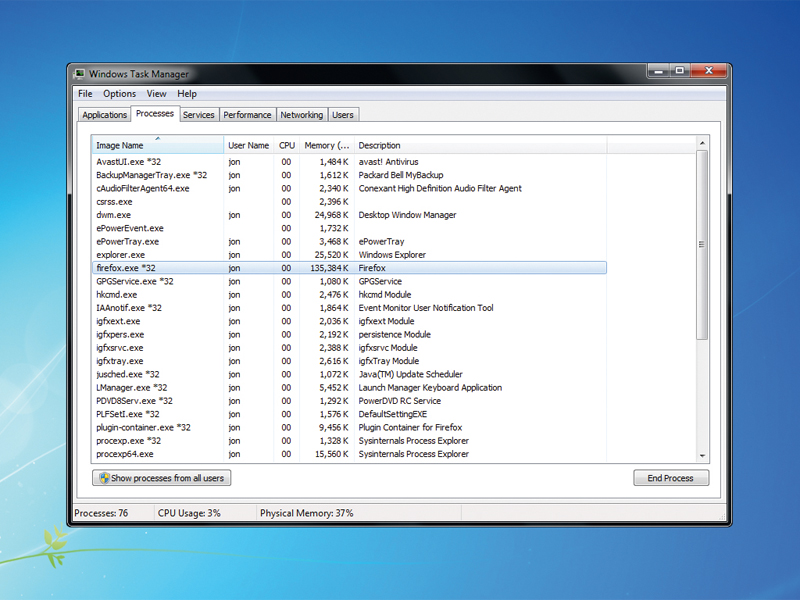
- If found, right-click on the process and select End Task
- Examine your files and file extensions:
- Look for files with unfamiliar extensions like .locky, .zepto, or .odin
- If you find such files, it is likely that your system is infected
- Check your desktop background and browser homepage:
- If your wallpaper has changed to a ransom note or your homepage redirects to a suspicious website, it indicates a ransomware infection
- Monitor network traffic:
- Use a reliable network monitoring tool to identify any unusual network connections or traffic
- Look for communication with known malicious IP addresses
Search for Ransomware Decryption Tools
If you have fallen victim to the Locky ransomware, you may be desperately searching for a way to restore your encrypted files. Luckily, there are decryption tools available that may be able to help you. These tools are designed to reverse the encryption process and recover your files without having to pay the ransom. To find these tools, you can visit websites like Bleeping Computer, which offers a variety of decryption tools for different types of ransomware. Once you have downloaded the tool, follow these steps: 1.
Disable any active antivirus programs 2. Run the decryption tool 3. Follow the on-screen instructions 4. Select the encrypted files you want to recover 5. Wait for the decryption process to complete Remember, these tools may not be able to decrypt all files, but they are definitely worth a try before considering paying the ransom.
Creating Data Backups
To protect your files from the Locky ransomware and other ransomware-type malware infections, it is crucial to create regular data backups. By regularly backing up your files, you can ensure that even if your computer gets infected, you won’t lose your important data.
Here’s how you can create data backups:
1. Identify the files you want to back up, such as documents, text files, and important photos.
2. Choose a reliable backup method, such as using an external hard drive, cloud storage, or network-attached storage (NAS).
3. Set up a regular backup schedule to ensure your files are backed up automatically.
4. Verify that your backups are working correctly and that you can access your files when needed.
5. Keep your backups disconnected from your computer or network to protect them from ransomware attacks.
6. Consider using multiple backup methods for added protection.
Remember, creating data backups is an essential step in protecting your files from ransomware attacks. Don’t wait until it’s too late – start backing up your data today and safeguard your valuable information.
Tips for Avoiding Locky Ransomware
- Keep your software up to date: Regularly update your operating system, antivirus software, and all other programs to ensure you have the latest security patches and protection against known vulnerabilities.
- Be cautious with email attachments: Exercise caution when opening email attachments, especially if they are from unknown or suspicious senders. Avoid opening any attachments that you were not expecting or that seem unusual.

- Enable macro security settings: Configure your email client and office suite to disable macros by default. Only enable macros in documents from trusted sources and when absolutely necessary.
- Beware of phishing attempts: Be vigilant and double-check the legitimacy of emails, especially those requesting personal information or directing you to click on links. Avoid clicking on suspicious links or providing sensitive data through email.
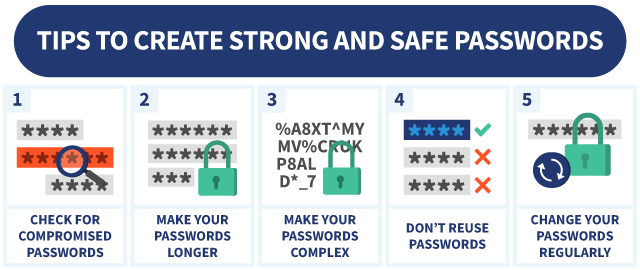
- Use strong, unique passwords: Create strong, complex passwords for all your accounts and avoid reusing them. Consider using a reliable password manager to securely store and manage your passwords.
- Backup your data regularly: Regularly backup your important files to an external hard drive, cloud storage, or another secure location. This ensures you can restore your data in case of a ransomware attack.
- Use reputable security software: Install and keep up-to-date a reputable antivirus/anti-malware solution that offers real-time protection against various threats, including ransomware.
- Exercise caution when browsing the web: Be cautious when visiting unfamiliar websites, especially those offering free downloads, pirated software, or suspicious content. Stick to reputable sources and be wary of pop-up ads.
- Keep a firewall enabled: Ensure your computer’s firewall is turned on to help block unauthorized access and potential malware infections.
- Stay informed about current threats: Stay up to date with the latest news and security alerts related to ransomware and other cyber threats. This knowledge can help you stay vigilant and take necessary precautions.
