Safeguarding your digital space has become an essential task in today’s interconnected world. In this article, we delve into the realm of easy zeroAccess Trojan removal, providing you with effective methods to protect your system from this notorious malware. Discover simple yet powerful techniques to ensure your online safety and bid farewell to the stealthy threats of the zeroAccess Trojan.
Removing ZeroAccess Trojan: Step-by-Step Guide
STEP 1: Power On your computer and log in to your desktop.
STEP 2: Download and install the latest version of Microsoft Security Essentials from the official website.
STEP 3: Open Microsoft Security Essentials and click on the “Scan Now” button.
STEP 4: Wait for the scan to complete. If any infected files are found, click on “Clean Computer” to remove them.
STEP 5: Restart your computer to complete the removal process.
STEP 6: After restarting, empty your recycle bin to permanently delete any remaining infected files.
By following these steps, you can effectively remove the ZeroAccess Trojan from your computer. Make sure to regularly update your antivirus software and be cautious when downloading files from the internet or opening email attachments to prevent future infections.
Starting your computer in Safe Mode with Networking
To start your computer in Safe Mode with Networking and remove the ZeroAccess Trojan, follow these steps:
1. Power on your computer and press the F8 key repeatedly until the Advanced Boot Options menu appears.
2. Use the keyboard arrows to highlight “Safe Mode with Networking” and press Enter.
3. Once your computer has booted into Safe Mode with Networking, open your web browser and download the latest version of the KB2895 tool from the Microsoft website.
4. Run the KB2895 tool to detect and remove the ZeroAccess Trojan from your computer.
5. After the tool has finished scanning and removing any infections, restart your computer in normal mode.
6. To ensure complete removal, it is recommended to run a full scan with your antivirus security software, such as Windows Defender or an anti-malware program.
7. If you are still experiencing issues or if the Trojan persists, seek professional assistance or consult online forums for further guidance.
Remember to regularly update your antivirus software and avoid downloading files or opening email attachments from untrusted sources to prevent future infections. Stay vigilant and protect your computer from malware threats.
Cleaning your computer from malicious threats
- Scan your computer: Use a reliable antivirus software to thoroughly scan your computer for any traces of the ZeroAccess Trojan.
- Update your antivirus: Ensure that your antivirus software is up to date with the latest virus definitions to effectively detect and remove the ZeroAccess Trojan.
- Disconnect from the internet: Unplug your computer from the internet to prevent the ZeroAccess Trojan from communicating with its command and control servers.
- Remove suspicious programs: Uninstall any unfamiliar or suspicious programs from your computer’s control panel that may be linked to the ZeroAccess Trojan.
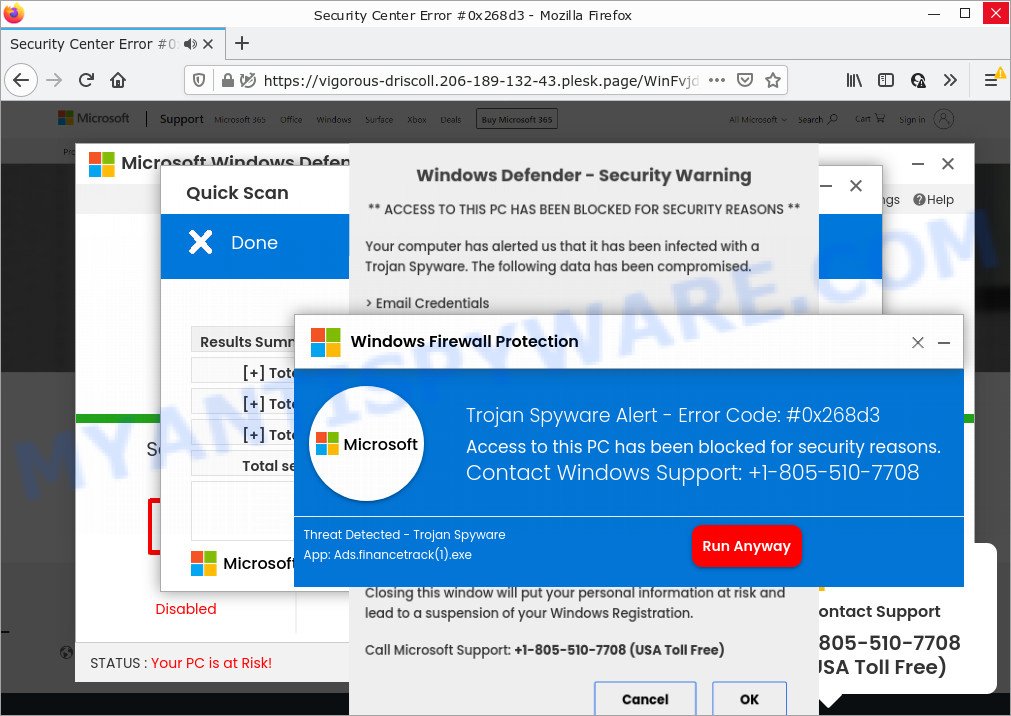
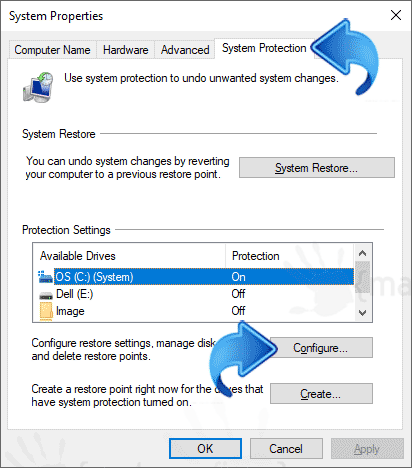
- Disable system restore: Temporarily disable the system restore feature on your computer to prevent the ZeroAccess Trojan from reappearing after removal.
- Delete malicious files: Manually delete any suspicious files or folders associated with the ZeroAccess Trojan from your computer’s directories.
- Clean your web browsers: Remove any suspicious extensions, plugins, or toolbars from your web browsers that may have been installed by the ZeroAccess Trojan.
- Change your passwords: Update your passwords for online accounts, including email, banking, and social media, to prevent unauthorized access by the ZeroAccess Trojan.
- Enable firewall protection: Activate your computer’s firewall to block any incoming connections from the ZeroAccess Trojan or other malicious threats.
- Regularly update your software: Keep all your software, including the operating system, web browsers, and plugins, up to date to ensure you have the latest security patches and protection against the ZeroAccess Trojan.
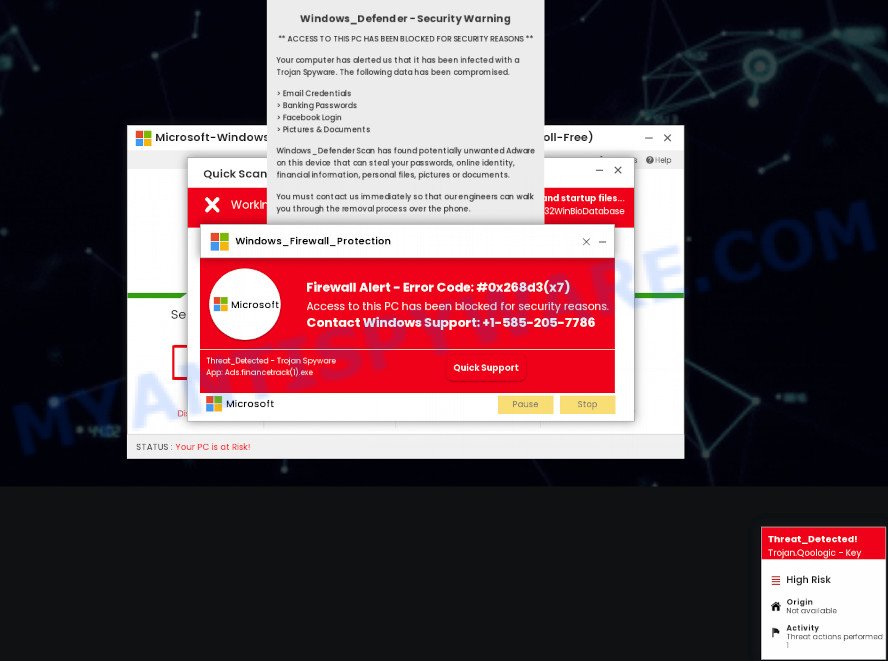
Removing ZeroAccess Trojan using specialized tools
Removing the ZeroAccess Trojan is a crucial step in ensuring the security of your computer. Fortunately, there are specialized tools available that can help with this process.
To begin, download a reputable anti-malware program such as Windows Defender or an anti-malware software from a trusted source. Run a full system scan to detect and remove any traces of the ZeroAccess Trojan.
STEP 1: Open the anti-malware program and navigate to the scan options. Select the full system scan and initiate the scan.
During the scan, the program will search for any files or components associated with the ZeroAccess Trojan, including rootkits and other malware applications. Once the scan is complete, follow the program’s instructions to remove the detected threats.
It is important to regularly update your anti-malware program to ensure it can detect the latest variants of the ZeroAccess Trojan. Additionally, practice safe browsing habits and avoid downloading files from untrusted sources, such as suspicious websites or email attachments.
By taking these steps, you can effectively remove the ZeroAccess Trojan from your computer and protect it from future infections.
Additional steps for thorough removal of ZeroAccess Trojan
- Step 1: Disconnect from the internet to prevent further spread of the ZeroAccess Trojan.
- Step 2: Run a full system scan using a reputable antivirus or antimalware program.
- Step 3: Quarantine or delete any detected ZeroAccess Trojan files or components.
- Step 4: Update your operating system and all installed software to their latest versions to patch any vulnerabilities.
- Step 5: Change all your passwords, especially for online banking, email, and social media accounts.
- Step 6: Enable or update your firewall to enhance your system’s security.
- Step 7: Be cautious when downloading files or clicking on links from unknown or suspicious sources.
- Step 8: Regularly backup your important files and data to an external storage device or cloud service.
- Step 9: Educate yourself and your family about safe internet practices, including recognizing phishing attempts and avoiding suspicious websites.
- Step 10: Consult with a cybersecurity professional or seek guidance from reputable online forums if you need further assistance or have concerns about your system’s security.