Unlocking the Mystery: A Comprehensive Guide to Eliminating Microsoft Security Essentials Ransomware
Introduction to Microsoft Security Essentials and Ransomware Removal
Microsoft Security Essentials is a powerful tool for removing ransomware from your PC. To begin, ensure that you have the latest version of Microsoft Security Essentials installed on your Windows 7 or Windows 8.1 computer.
To start the removal process, open Microsoft Security Essentials by clicking on the shield icon in the notification area. From there, navigate to the “Scan” tab and choose your scan options. It’s important to select a full scan to thoroughly check your system for any malicious software.
After the scan is complete, review the results and quarantine any detected ransomware or viruses. You can do this by selecting the malicious files and clicking on the “Quarantine” button.
Remember to regularly update Windows and Microsoft Security Essentials to stay protected against the latest threats. Additionally, be cautious of suspicious emails, file attachments, and websites, as these can be common sources of ransomware.
For enhanced protection, consider using Windows Defender Antivirus or the Microsoft Defender Antivirus included in Windows 10. These tools offer advanced ransomware detection and removal capabilities.
By following these steps and utilizing the resources provided by Microsoft, you can effectively remove ransomware from your PC and keep your files and information secure.
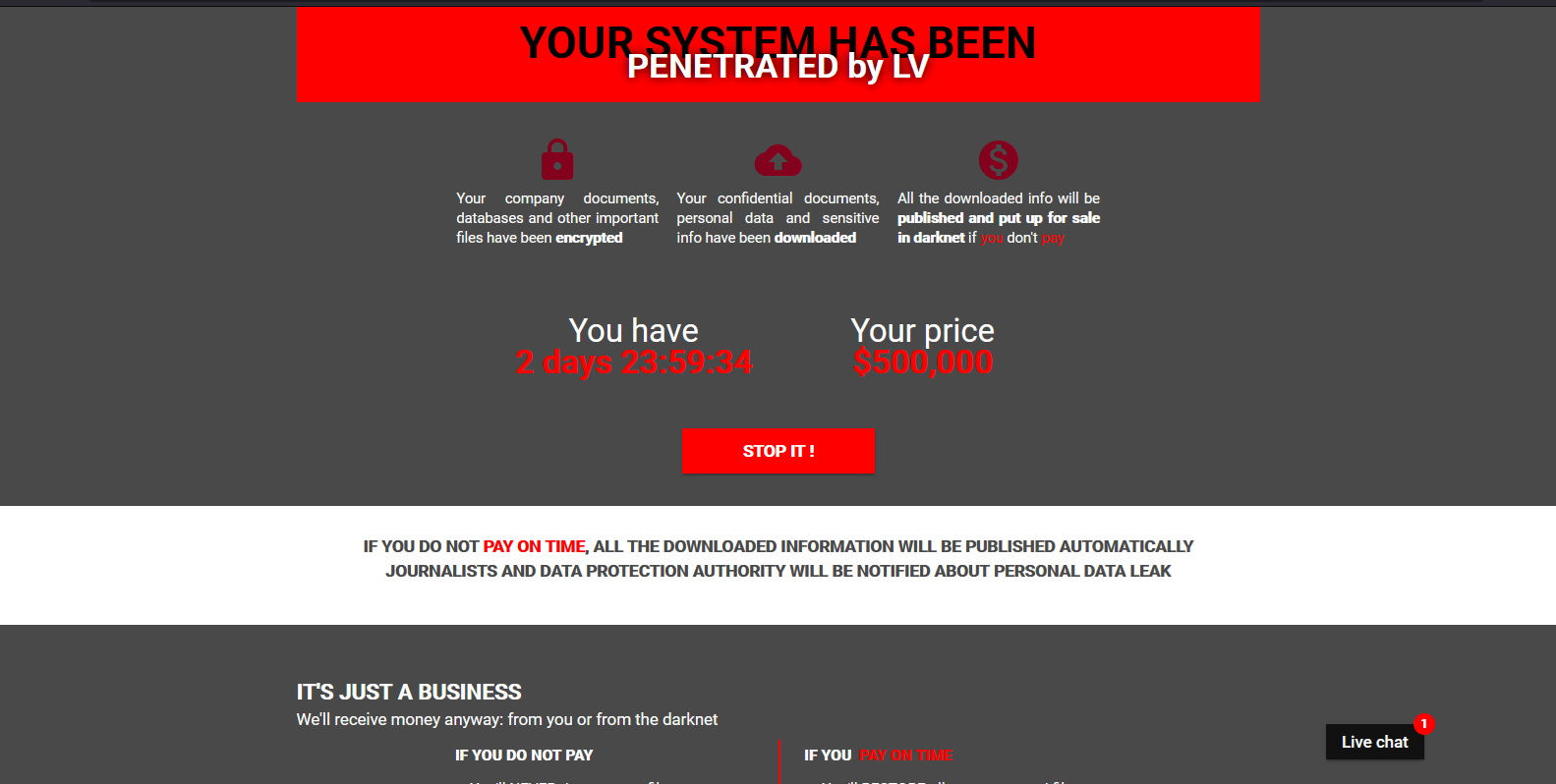
Symptoms of Ransomware Infection
- Identify the symptoms of a ransomware infection:
- Locked or encrypted files
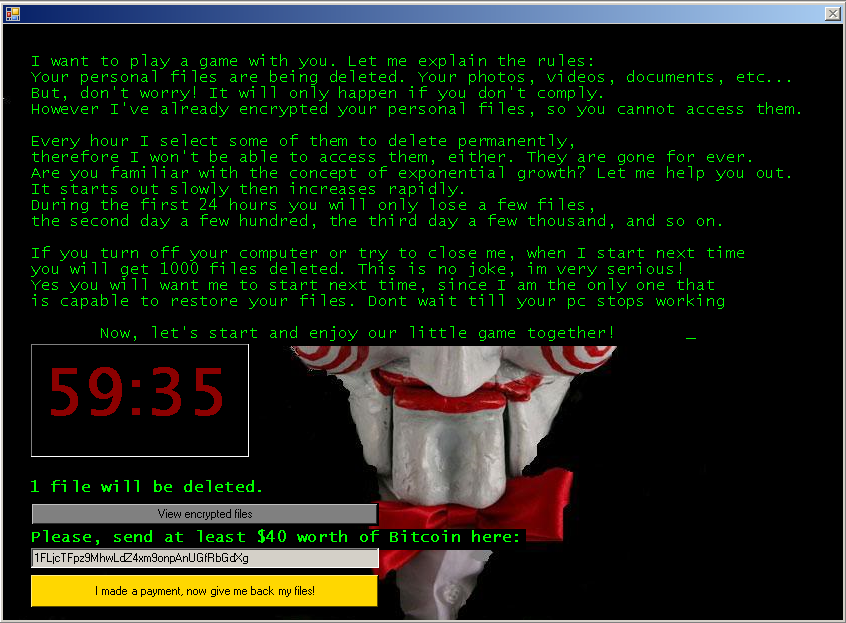
- Ransom note or message demanding payment
- Unusual system behavior
- Unresponsive programs or slow performance
- Pop-up windows or advertisements
- Disconnect from the network:
- Physically disconnect from the internet by unplugging the network cable or disabling Wi-Fi
- Prevent further encryption or data loss by isolating the infected system
- Identify the ransomware variant:
- Research the ransom note or message for any specific indicators or names
- Use online resources or security forums to identify the ransomware variant
- Report the ransomware infection:
- Contact your organization’s IT department or IT service provider
- Inform them about the ransomware infection and provide any details or indicators you have
- Cooperate with their instructions and follow their guidance
- Do not pay the ransom:
- There is no guarantee that paying the ransom will result in the recovery of your files
- Supporting criminal activities by paying the ransom

- Encouraging future ransomware attacks
- Remove the ransomware:
- Use reputable antivirus or anti-malware software to scan and remove the ransomware
- Update the antivirus software to ensure it has the latest virus definitions
- Perform a full system scan and follow the software’s instructions to remove the ransomware
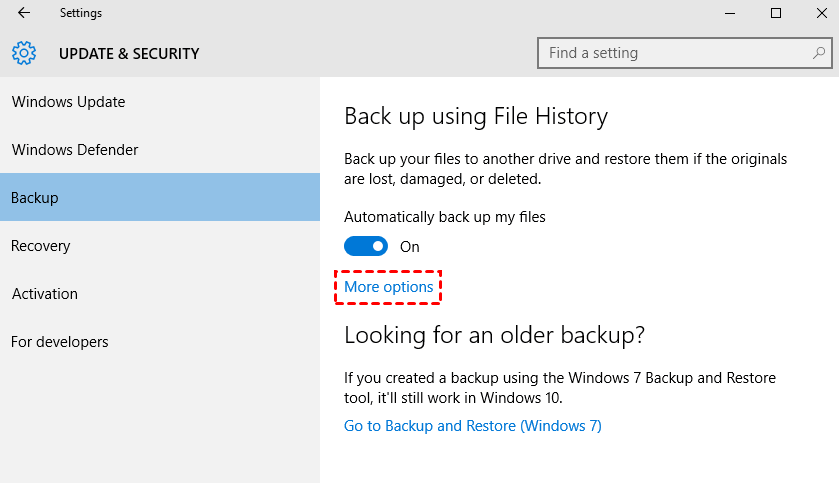
- Restore files from backups:
- If you have backups of your files, restore them after ensuring the ransomware is removed
- Follow the backup restoration process provided by your organization’s IT department or IT service provider
- Ensure the backups are clean and free from any malware before restoring
- Strengthen security measures:
- Update all software and operating systems to the latest versions
- Install reputable antivirus software and keep it updated
- Enable automatic system updates
- Regularly back up important files and verify the backups regularly
- Educate yourself and your organization about safe online practices and how to recognize potential threats
- Monitor for any suspicious activity:
- Keep an eye on your system and files for any unusual behavior or signs of reinfection
- If you notice any suspicious activity, report it to your organization’s IT department or IT service provider
- Stay vigilant and continue practicing good cybersecurity hygiene
Microsoft Security Tools for Protection
Microsoft Security Essentials Ransomware Removal Guide
| Tool | Description |
|---|---|
| Windows Defender Offline | A bootable tool that scans your computer for malware without requiring an active operating system. |
| Microsoft Safety Scanner | A downloadable tool that scans your computer for viruses, spyware, and other malicious software. |
| Windows Malicious Software Removal Tool | A tool that checks your computer for infections by specific, prevalent malicious software and helps remove them. |
| Microsoft Enhanced Mitigation Experience Toolkit (EMET) | A utility that helps prevent vulnerabilities in software from being successfully exploited. |
| Microsoft Baseline Security Analyzer (MBSA) | A tool to assess the security state of your computer based on Microsoft security recommendations. |
| Windows Update | Regularly installing Windows updates helps keep your computer secure by patching vulnerabilities. |
python
import os
def remove_ransomware(directory):
for root, dirs, files in os.walk(directory):
for file in files:
file_path = os.path.join(root, file)
# Implement logic to identify ransomware files based on some characteristics
# For example, check for file extensions, presence of ransom notes, etc.
if is_ransomware(file_path):
os.remove(file_path)
print(f"Ransomware file removed: {file_path}")
def is_ransomware(file_path):
# Implement logic to identify ransomware files based on specific characteristics
# For example, check for particular file extensions or analyze file contents
# This logic would vary depending on the type of ransomware being targeted
return False
# Usage example
directory_to_scan = "C:\Users\YourUsername\Documents"
remove_ransomware(directory_to_scan)
Please note that the code above is a basic example and is not intended to be a fully functional ransomware removal tool. It only demonstrates the concept of scanning files in a directory and removing files that meet certain criteria. For real-world ransomware removal, it is highly recommended to use professional security software developed by experts in the field.
Updating and Using Microsoft Security Essentials
Updating and using Microsoft Security Essentials is crucial for protecting your computer from ransomware. To update Microsoft Security Essentials on Windows 7 or Windows 8.1, follow these steps:
1. Open Microsoft Security Essentials by clicking on the icon in the taskbar or by searching for it in the Start menu.
2. Click on the “Update” tab and then click on the “Update definitions” button. This will ensure that you have the latest security updates to detect and remove ransomware.
To use Microsoft Security Essentials to scan and remove ransomware, follow these steps:
1. Open Microsoft Security Essentials and click on the “Home” tab.
2. Click on the “Scan options” button and choose the desired scan type: Quick scan, Full scan, or Custom scan.
3. Click on the “Scan now” button to start the scan. Microsoft Security Essentials will scan your computer for any ransomware or other malicious software.
4. After the scan is complete, review the results to see if any threats were detected.
5. To remove any detected ransomware, click on the “Clean computer” button. Microsoft Security Essentials will remove the ransomware and quarantine any infected files.
Remember to regularly update and use Microsoft Security Essentials to keep your computer protected from ransomware and other threats.
Using Windows Defender and Microsoft Security Essentials for Scanning
To protect your computer from ransomware, it’s important to regularly scan your system using Windows Defender and Microsoft Security Essentials. These scanning tools are designed to detect and remove malicious software, including ransomware.
To start a scan, open Windows Defender or Microsoft Security Essentials and navigate to the “Scan” tab. Click on the “Full Scan” option to thoroughly scan your entire computer for any potential threats.
During the scan, the software will check all files, folders, and programs on your computer for any signs of malware. If any threats are detected, Windows Defender or Microsoft Security Essentials will prompt you to take action.
Follow the instructions provided to quarantine or remove the detected malware. If you’re unsure about a specific file or program, you can exclude it from the scan by adding it to the exclusions list.
Remember to regularly update Windows Defender or Microsoft Security Essentials to ensure you have the latest security updates and enhanced protection against ransomware and other threats.
By regularly scanning your computer with these powerful tools, you can help safeguard your data and protect against potential ransomware attacks.
Additional Help and Options for Ransomware Removal
- Update Windows: Make sure your operating system is fully updated with the latest security patches to protect against ransomware attacks.
- Install and Update Microsoft Security Essentials: Download and install the latest version of Microsoft Security Essentials, our free antivirus software, to detect and remove ransomware.

- Perform a Full System Scan: Run a thorough scan of your computer to identify and eliminate any malicious files or programs associated with ransomware.
- Enable Windows Firewall: Activate the built-in Windows Firewall to add an extra layer of protection against ransomware and other cyber threats.
- Enable Automatic Updates: Ensure that your Microsoft Security Essentials and Windows Firewall are set to automatically update to stay protected against emerging ransomware threats.
- Backup Your Files: Regularly back up your important files to an external hard drive or cloud storage service to prevent data loss in case of a ransomware attack.
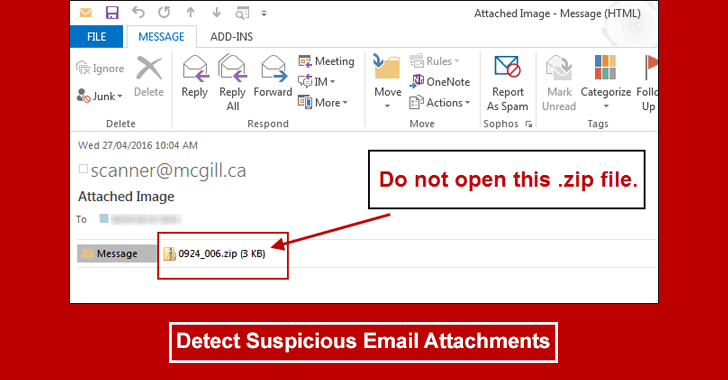
- Be Cautious of Suspicious Emails and Links: Avoid clicking on links or opening email attachments from unknown senders, as these could be sources of ransomware infections.
- Use Microsoft Edge or Internet Explorer with SmartScreen Filter: Enable SmartScreen Filter in your browser settings to block malicious websites and downloads.
- Stay Informed: Keep up-to-date with the latest ransomware trends and security best practices to protect yourself and your devices from evolving threats.
- Report Ransomware Incidents to Microsoft: If you have encountered a ransomware attack, report the incident to Microsoft so we can investigate and provide appropriate support.
Recognizing and Dealing with Ransomware Attacks
If you suspect a ransomware attack on your Windows computer, take immediate action to minimize damage. Disconnect from the internet and backup important files to prevent further encryption.
To remove ransomware using Microsoft Security Essentials, follow these steps:
1. Start your computer in Safe Mode by pressing and holding the Shift key while selecting Restart from the Power menu in the Start menu.
2. Launch Microsoft Security Essentials.
3. Enter the scanning tools by clicking on the “Scan” tab.
4. Perform a Full Scan to thoroughly check your system for any malware.
5. Quarantine any detected malware by clicking on the “Quarantine” tab.
6. Use the “Remove” option to permanently delete the malware from your computer.
7. Regularly update Windows, your antivirus software, and other apps to ensure the latest security patches are installed.
8. Be cautious when opening email attachments or visiting unfamiliar webpages.
9. Avoid downloading files from untrusted sources or clicking on suspicious links.
10. Consider using Windows Defender Antivirus or Office 365 to enhance ransomware detection and protection.
By following these steps, you can effectively identify and remove ransomware from your Windows computer, protecting your files, data, and personal information.
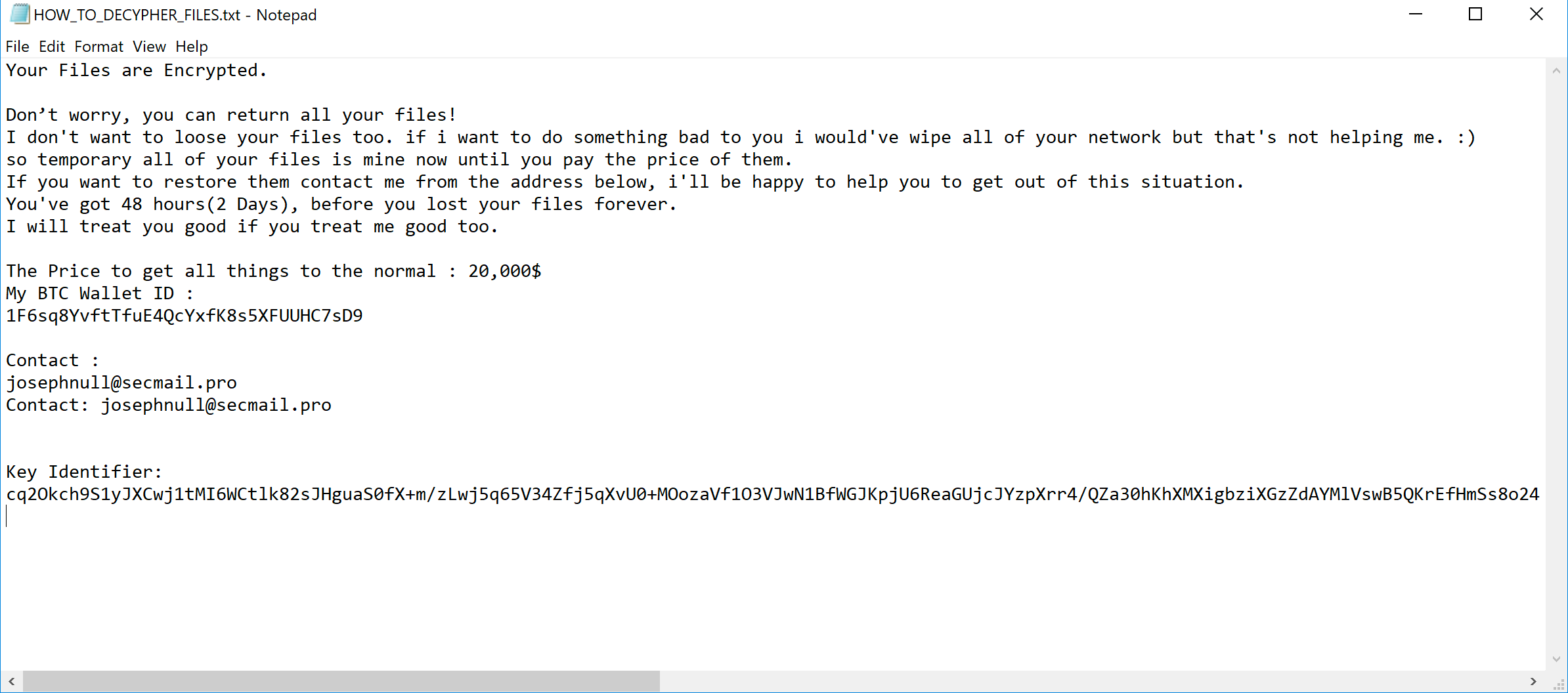
What to Do if You’ve Been Infected or Paid the Ransom
If you’ve been infected with ransomware or have paid the ransom, follow these steps to remove it and restore your files.
1. Disconnect from the internet immediately to prevent further damage.
2. Use a reliable virus scanner, like Microsoft Security Essentials, to scan your computer for malware.
3. If any threats are detected, quarantine them to prevent further spread.
4. Use system tools, like Windows Update, to ensure your operating system is up to date.
5. Restore your files from a backup, if available. Be cautious with file attachments and webpages.
6. Change your passwords for all accounts to prevent unauthorized access.
7. Consider reporting the incident to local authorities and your antivirus software provider.
8. Learn from the experience and take steps to prevent future infections, such as using strong passwords and being cautious with downloads.
Remember, Microsoft Security Essentials and regular backups are essential for protecting your computer and files. Stay vigilant and stay safe.
Resources for Preventing and Handling Ransomware Infections
- Stay Updated: Regularly update your operating system, security software, and applications to protect against the latest ransomware threats.
- Enable Automatic Updates: Enable automatic updates to ensure your system receives the latest security patches and updates.

- Use a Reliable Antivirus: Install and maintain a reputable antivirus program, such as Microsoft Security Essentials, to detect and remove ransomware.
- Back up Your Data: Regularly back up your important files and data to an external storage device or cloud service.
- Exercise Caution: Be vigilant while browsing the web or opening email attachments. Avoid clicking on suspicious links or downloading files from untrusted sources.
- Enable Firewall: Ensure your firewall is turned on to add an extra layer of protection against unauthorized access.
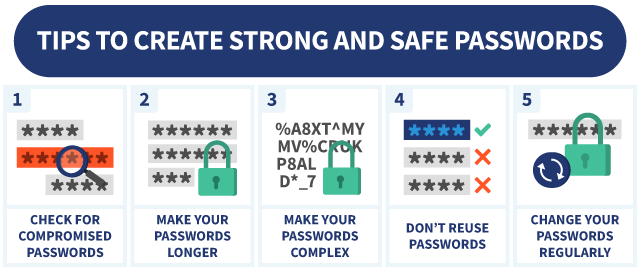
- Use Strong, Unique Passwords: Create strong passwords for your online accounts and avoid reusing passwords across multiple platforms.
- Enable Pop-up Blocker: Prevent malicious pop-ups from infecting your system by enabling the pop-up blocker feature in your browser.
- Be Wary of Social Engineering Tactics: Be cautious of unsolicited emails, phone calls, or messages that request sensitive information or urge immediate action.
- Secure Remote Desktop Protocol (RDP): If using RDP, ensure it is properly configured with strong passwords and limited access.
- Scan Attachments: Scan email attachments and downloaded files using your antivirus software before opening them.
- Implement Least Privilege: Limit user privileges to minimize the potential impact of a ransomware infection.
- Regularly Educate Users: Train employees or family members about safe computing practices and how to identify and avoid potential ransomware threats.
- Utilize Windows Defender Antivirus: Windows users can benefit from the built-in Windows Defender Antivirus, which provides real-time protection against ransomware and other threats.
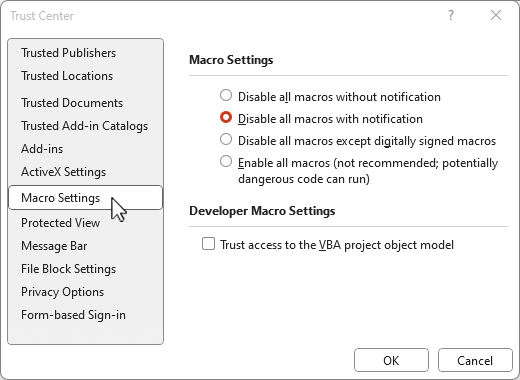
- Disable Macros in Office Files: Disable macros in Microsoft Office files, as they can be exploited to deliver ransomware.
- Utilize Microsoft Safety Scanner: Periodically run the free Microsoft Safety Scanner to detect and remove any existing ransomware infections.